Home > software_development > Input Validation and its Role In Preventing Cyber Attacks
Input Validation and its Role In Preventing Cyber Attacks
Input validation represents one of the most essential yet often overlooked components of digital security and functionality.
By :Thomas Inyang🕒 19 May 2025
Introduction
The flow of data between systems and users has posed serious security concerns, and to ensure the integrity and security of information, one needs to consider input validation.
This concept cuts across different fields: a developer building robust applications, a cybersecurity professional safeguarding systems, or someone who protects online data. Input validation represents one of the most essential yet often overlooked components of digital security and functionality.
At the end of this article, you will be familiar with the following:
- What input validation is and the category and types.
- The purpose and importance of validation.
- The difference between validation and verification
- How to handle validation
What Is Input Validation? Understanding the Foundation of Data Security
This is the process of verifying data entering a system meets specified requirements and constraints before processing it further. This process ensures that only properly formatted, expected data is accepted by applications, thereby preventing errors, system vulnerabilities, and potential security breaches.
This data could be user inputs from form fields, API responses, file uploads, or any other information originating outside the system's boundaries.
When we talk about validation in computing, we're discussing the critical process that examines whether input data conforms to expected parameters regarding type, length, format, and value range. Think of it as a digital gatekeeper that inspects every piece of incoming information, allowing only legitimate data to proceed while rejecting or sanitizing potentially problematic inputs.
Beyond the terms already mentioned, input validation is sometimes called input sanitization, data verification, or input checking.

What are the Types of Input Validation
There are distinct methodologies used to verify data, including client-side validation (performed in the browser for immediate feedback through JavaScript or HTML5 validation attributes), server-side validation (performed on the server for security that cannot be bypassed by disabling browser features), syntactic validation (checking format rules like email addresses containing "@" symbols), and semantic validation (checking logical validity like birth dates not being in the future).
While categorizations may vary among experts, a common framework includes the following:
- Format validation—checking if data follows required patterns (e.g., postal codes, phone numbers).
- Range validation—ensuring numeric values fall within acceptable limits.
- Consistency validation—verifying related data fields are logically compatible (e.g., start dates preceding end dates).
- Database validation—confirming data against existing records (e.g., checking if a username already exists).
User input can be validated using the following approaches:
- Regular expression testing—using pattern matching to verify format conformity.
- Type checking—ensuring inputs match expected data types (numbers, strings, etc.).
- Boundary analysis - Verifying values fall within acceptable minimum and maximum ranges
What is The Purpose and Importance of Input Validation?
It prevents malformed or malicious data from compromising system functionality, security, and data integrity by enforcing proper data formats, types, and values before processing inputs further in the application workflow. It also serves multiple objectives:
- Security enhancements to prevent injection attacks, cross-site scripting, and other vulnerabilities that exploit unvalidated inputs.
- Prevents error by reducing system crashes and unexpected behaviors caused by improper data formats.
- Ensuring information in databases remains accurate and consistent and providing immediate feedback when input requirements aren't met.
Proper validation acts as a shield against the following threats:
- SQL injection attacks—preventing malicious code insertion into database queries.
- Cross-site scripting, blocking attackers from injecting client-side scripts.
- Stopping excessive data inputs that can crash applications, such as buffer overflows.
- Preventing manipulation of application processes through unexpected inputs that attack the business logic.
- Maintaining database integrity by ensuring valid entries that won’t corrupt the data.
How is input validation advantageous? It is important in the following ways:
- It helps users provide correct information through clear feedback.
- Reduced support costs—minimizing issues caused by uncleaned data and ensuring more stable and predictable application behavior.
- Regulatory compliance—meeting data protection requirements in various industries and preventing security incidents that could damage organizational trust.
What is the difference between verification and validation input?
While input validation confirms that data meets format and type requirements before processing, verification determines whether the data is factually accurate and appropriate for its intended purpose—together forming a comprehensive approach to data quality assurance.
Though often used interchangeably, these terms represent distinct concepts in data quality management:
- Validation answers the question, "Is this data properly formatted and within acceptable parameters?"
- Verification addresses, "Is this data factually correct and appropriate for its purpose?"
For example, an email address field can be validated to confirm it contains an "@" symbol and follows proper format, but only verification (perhaps through a confirmation email) can determine if it's actually a working address belonging to the intended user.
Another key distinction involves timing: validation typically happens during data entry or transmission, while verification might occur later through comparison with existing records or external sources.
Where and How to Validate Data
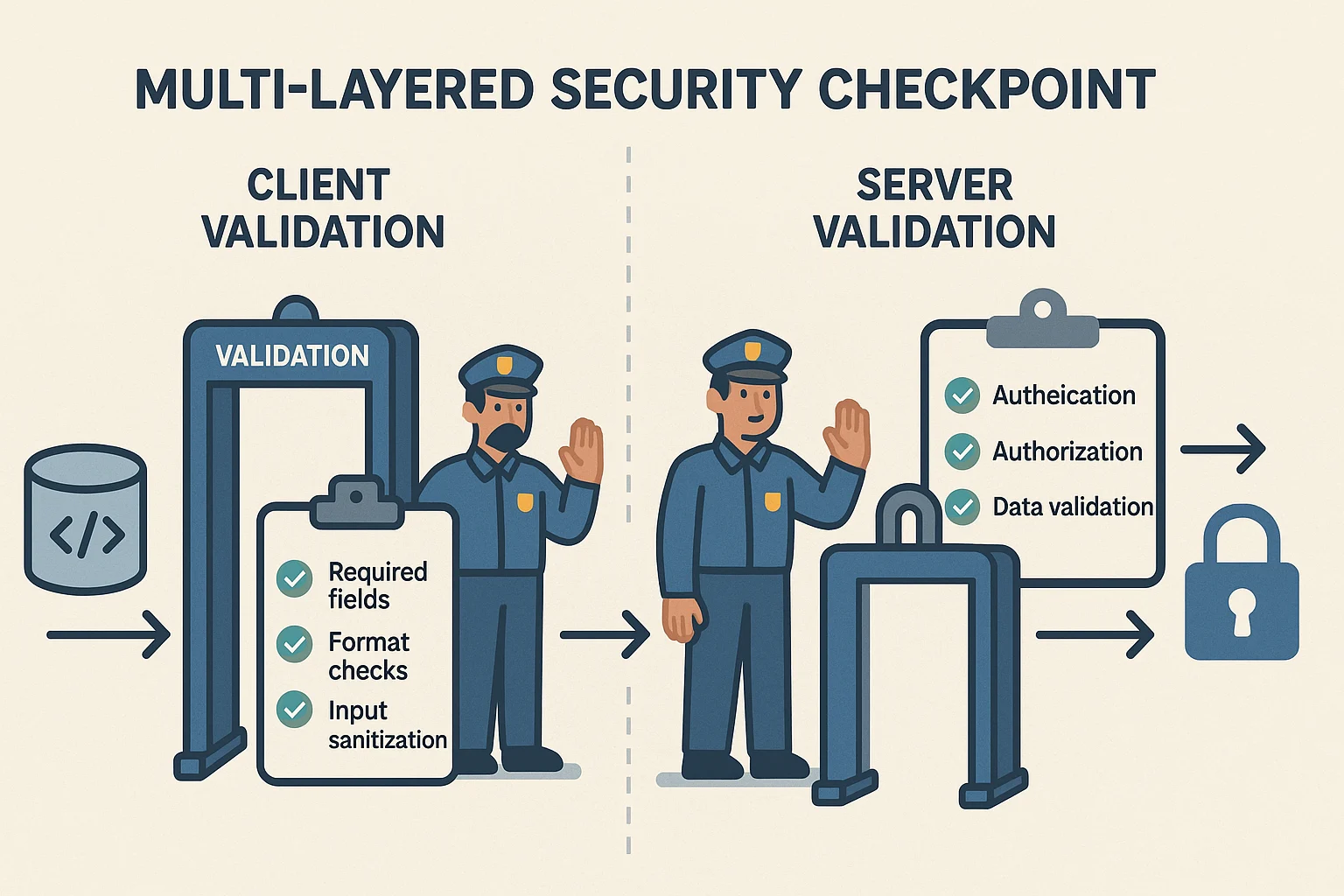
Input validation implementation involves deploying validation checks at multiple points in an application's architecture, using techniques like regular expressions, type checking, and constraint enforcement to verify data before processing, with both client-side and server-side validation working together for optimal security and user experience.
The gold standard in modern application development is implementing validation at multiple levels:
- Client-side validation—in the browser using JavaScript, HTML5 attributes, or frontend frameworks.
- Server-side validation—on the backend, regardless of client validation results.
- API gateway level—for services receiving requests from various clients.
- Database level - Using constraints to ensure data integrity as a final safeguard
While client-side validation improves user experience by providing immediate feedback, server-side validation is non-negotiable since client validations can be bypassed or manipulated. Implementation typically involves several approaches:
- Using built-in validation features of development frameworks and libraries (Joi).
- Implementing regular expressions to check if inputs match expected patterns.
- Creating validation functions that check inputs against business rules.
- Employing validation libraries that offer pre-built validation rules.
- Setting up database constraints as a final defense layer.
In application workflows, validation should be implemented as a sequential process:
- Initial validation occurs when data is first received.
- Contextual validation checks relationships between different input fields.
- Business logic validation ensures inputs make sense for specific operations.
- Pre-processing validation performs final checks before committing data.
How do you validate input numbers? Numeric validation typically involves several checks:
- Type checking—ensuring the input is actually numeric.
- Verifying numbers that fall within acceptable boundaries.
- Format validation—checking for proper decimal places or numeric patterns.
- Logic validation - Confirming numbers make sense in context (e.g., quantities can't be negative)
How do I validate input files? File validation requires a multi-layered approach:
- Validating file extensions against a whitelist of permitted types.
- Checking MIME types to verify file content matches the extension.
- Scanning for malicious content using security tools.
- Validating file size to prevent denial-of-service attacks.
- Verifying file integrity through checksums when appropriate
What are The Risks and Challenges on Input Validation?
The risks arise when validation mechanisms are inadequate, improperly implemented, or bypassed, potentially leading to security vulnerabilities, data corruption, or system failures that can be exploited by attackers or cause application malfunctions. The following risk emerges:
- Security vulnerabilities open the door to various attack vectors.
- Data corruption can occur when invalid information enters databases.
- System instability results from applications processing unexpected inputs.
- Business logic flaws allow circumvention of intended application workflows.
- Compliance violations may arise when regulated data isn't properly validated.
Beyond the risks of inadequate validation, even well-intentioned validation can create problems when the following occurs:
- Overly strict validation prevents legitimate use cases.
- Validation rules don't account for international formats (like address formats and phone numbers).
- Error messages reveal too much information about the system's structure.
- Validation introduces significant performance impacts by implementing overly complex checks.
How to Handle Validation Errors Effectively and Respond to Input Problems
It is a process of detecting, communicating, and resolving instances where input data fails to meet specified requirements, involving clear error messaging, appropriate logging, graceful failure modes, and user-friendly remediation guidance.
Validation errors typically occur when user inputs don't meet requirements, format specifications aren't followed, business rules are violated, system constraints are exceeded, and malicious input attempts are detected.
When you encounter an "input validation failed" message, it indicates the system has rejected data because it doesn't satisfy validation rules. This generic message often requires more details about which validation checks failed and why.
When validation mechanisms appear to malfunction, carry out the following troubleshooting: Verify the validation code is executing correctly, ensure it matches current requirements, look for unexpected formats or edge cases, check if validation can be circumvented, and ensure errors are being properly caught and communicated.
Input Validation vs. Other Security Concepts: Complementary Approaches
While input validation focuses on verifying that data meets format and type requirements before processing, it works alongside complementary security measures like input sanitization (cleaning potentially harmful content), authentication (verifying identity), and access control (managing permissions) to form a comprehensive security strategy.
For example, validation might reject a string containing script tags as invalid, while sanitization would strip those tags while accepting the remaining content.
In the context of validation, testing involves systematically verifying that validation rules work correctly across various scenarios, while debugging focuses on identifying and fixing issues when validation doesn't behave as expected.
See Also: How to Test a Node.js Backend Application.
Data verification extends beyond basic validation to establish factual correctness:
- Cross-referencing with authoritative sources or existing records.
- Multi-factor verification requiring confirmation through separate channels.
- Cryptographic verification checking digital signatures or hashes.
- Human verification involving manual review processes.
- Temporal verification confirming data remains valid over time.
Balancing Validation: Finding the Right Approach
Effective input validation strikes a balance between security and usability, implementing sufficient safeguards to protect systems while avoiding excessive restrictions that hamper legitimate users, requiring thoughtful design that considers both technical requirements and user experience.
Like most security measures, validation's value depends on implementation:
Positive aspects include:
- Protects systems from malicious and malformed inputs
- Prevents data quality issues throughout applications
- Guides users toward providing correct information
- Reduces errors and improves system stability
Potential drawbacks include:
- Can frustrate users when implemented poorly
- May block legitimate but unusual inputs without proper design
- Introduces additional processing overhead
- Requires ongoing maintenance as requirements evolve
The key is finding appropriate balance—validation that provides security without imposing unnecessary restrictions.
While security often dominates the discussion, many practitioners consider data quality the primary benefit—preventing "garbage in, garbage out" scenarios that undermine system reliability and trustworthiness.
Conclusion
As technologies evolve, input validation continues to adapt to new challenges and opportunities. Modern approaches increasingly leverage machine learning to identify anomalous inputs, context-aware validation that adjusts based on user behavior patterns, and standardized validation frameworks that enhance security while reducing implementation burdens.
For developers, security professionals, and organizations, input validation represents more than just a technical requirement—it embodies a commitment to data integrity, system security, and user experience. By implementing thoughtful, comprehensive validation strategies, we contribute to a more secure, reliable digital ecosystem for all users.
Whether you're building new systems, securing existing applications, or simply interested in how your data remains protected online, understanding input validation is one of the fundamental building blocks of digital trust.
Remember that effective validation is drastically evolving—what constitutes "best practice" today may change tomorrow as new threats emerge and user expectations evolve. The most successful validation approaches maintain security while adapting to changing requirements, ultimately serving the dual purposes of protection and usability that make digital systems both safe and accessible.
Please Share and Comment