Home > software_development > What You Need to Know About XSS (Cross-Site Scripting).
What You Need to Know About XSS (Cross-Site Scripting).
Cross-Site Scripting (XSS attack) remains one of the most persistent security challenges in web development despite being well understood for many years.
By :Thomas Inyang🕒 17 May 2025

Introduction
When it comes to web application security threats, Cross-Site Scripting (XSS) remains one of the most persistent and dangerous vulnerabilities.
This article covers XSS attacks in detail—from understanding what they are and how they work to implementing effective prevention strategies. Irrespective of your domain in the tech space—developer, security professional, or simply interested in cybersecurity—this article will equip you with essential knowledge to protect against these pervasive threats.
At the end of this article, you will learn the following:
- What XSS is and how it works.
- Types of Xss attacks
- XSS and other security vulnerabilities.
- The languages used in XSS attacks.
- XSS risk assessment and impact.
- How to prevent XSS attacks and best practices.
What is XSS and How Does It Work?
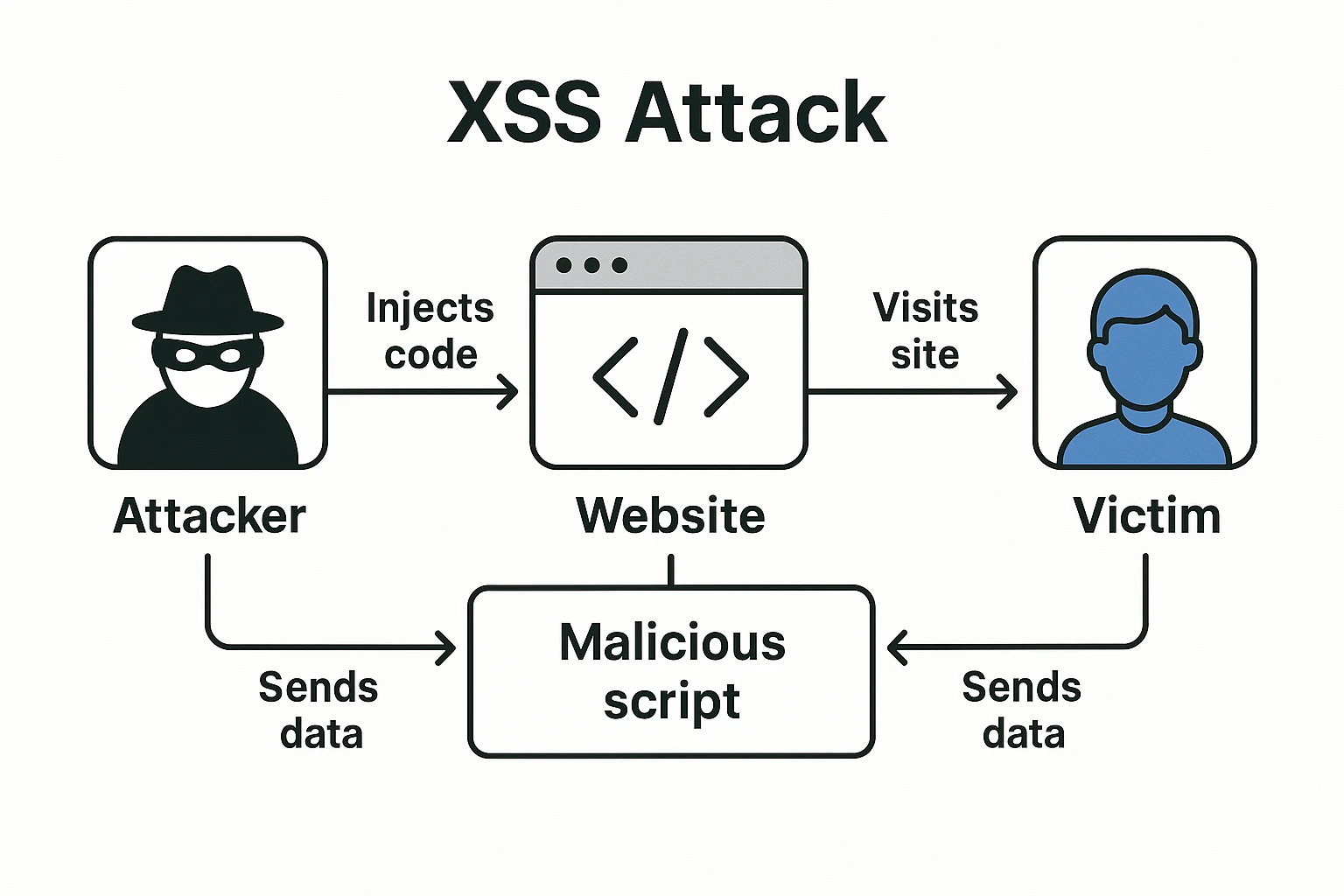
Cross-Site Scripting (XSS) is a type of security vulnerability that allows attackers to inject malicious client-side scripts into web pages viewed by other users. These scripts are executed in the victim's browser with the same privileges as legitimate scripts from the site, enabling attackers to steal sensitive information, manipulate web content, or perform actions on behalf of the victim.
Despite being well-documented for over two decades, XSS vulnerabilities continue to plague websites across the internet. But what exactly is XSS, and how does it work? At its core, XSS occurs when an application includes untrusted data in a web page without proper validation or encoding. A malicious script executes in their browser within the context of the vulnerable site and gives the attacker access to any information the browser handles for that site, including cookies, session tokens, and sensitive personal information.
See Also: How to Implement Cookies in a Backend Application.
The attack mechanism is relatively straightforward:
- The attacker identifies a website that doesn't properly sanitize user input
- They inject malicious JavaScript code into the vulnerable entry point
- When other users access the compromised page, the malicious script executes automatically
Consider a simple example: Imagine a forum that allows users to post comments. If the forum doesn't properly sanitize input, an attacker could post a comment containing malicious JavaScript code:
When other users view this comment, the script runs in their browsers, sending their cookies to the attacker's server. With these stolen cookies, the attacker might be able to hijack the victims' sessions and gain unauthorized access to their accounts.
Types of XSS Attacks: Understanding the Three Main Variants
There are three primary types of XSS attacks: Reflected XSS (where malicious script is reflected off a web server to a victim via URL parameters), Stored XSS (where the malicious code is permanently stored on the target server), and DOM-based XSS (where the vulnerability exists in client-side JavaScript rather than server-side code).
When discussing the different types of XSS attacks, security professionals typically identify three main categories. Understanding these variants is crucial for implementing appropriate defensive measures, as each type has distinct characteristics and attack vectors. Let’s see them in detail.
Reflected XSS Attacks
Reflected XSS, also known as non-persistent XSS, occurs when an attacker tricks a victim into clicking a specially crafted link containing malicious code. The vulnerable application "reflects" this code back to the user's browser, which then executes it.
In this type of attack, the malicious payload isn't stored on the website itself but is delivered through manipulated URLs, often distributed through phishing emails or malicious links on other websites. An example of reflected XSS might look like this:
https://vulnerable-site.com/search?query=<script>alert('XSS')</script>
If the search results page displays the query without proper sanitization, the script would execute when a user clicks the link.
Stored XSS Attacks
Stored XSS (also called persistent XSS) represents the most dangerous type of XSS. In this attack, the malicious script is permanently stored on the target server—often in a database—and is later retrieved and displayed to users during normal browsing. Common targets include comment sections, user profiles, forum posts, and product reviews.
The persistent nature of this attack makes it particularly dangerous, as the malicious script can affect many users without requiring them to click on specially crafted links.
A typical example is an attacker submitting a blog comment containing hidden JavaScript that steals authentication tokens.
DOM-based XSS Attacks
This type of attack is a more sophisticated variant where the vulnerability exists in the client-side JavaScript code rather than the server-side code. The attack occurs when client-side scripts modify the Document Object Model (DOM) in an unsafe way.
See Also: How and Where to Write Javascript Event Handler
Unlike the other types, DOM-based XSS doesn't necessarily involve sending malicious content to the server. Instead, it manipulates the client-side JavaScript environment directly. This makes DOM-based XSS particularly challenging to detect through traditional security scanning tools that focus on server responses.
XSS vs. Other Security Vulnerabilities: Key Differences
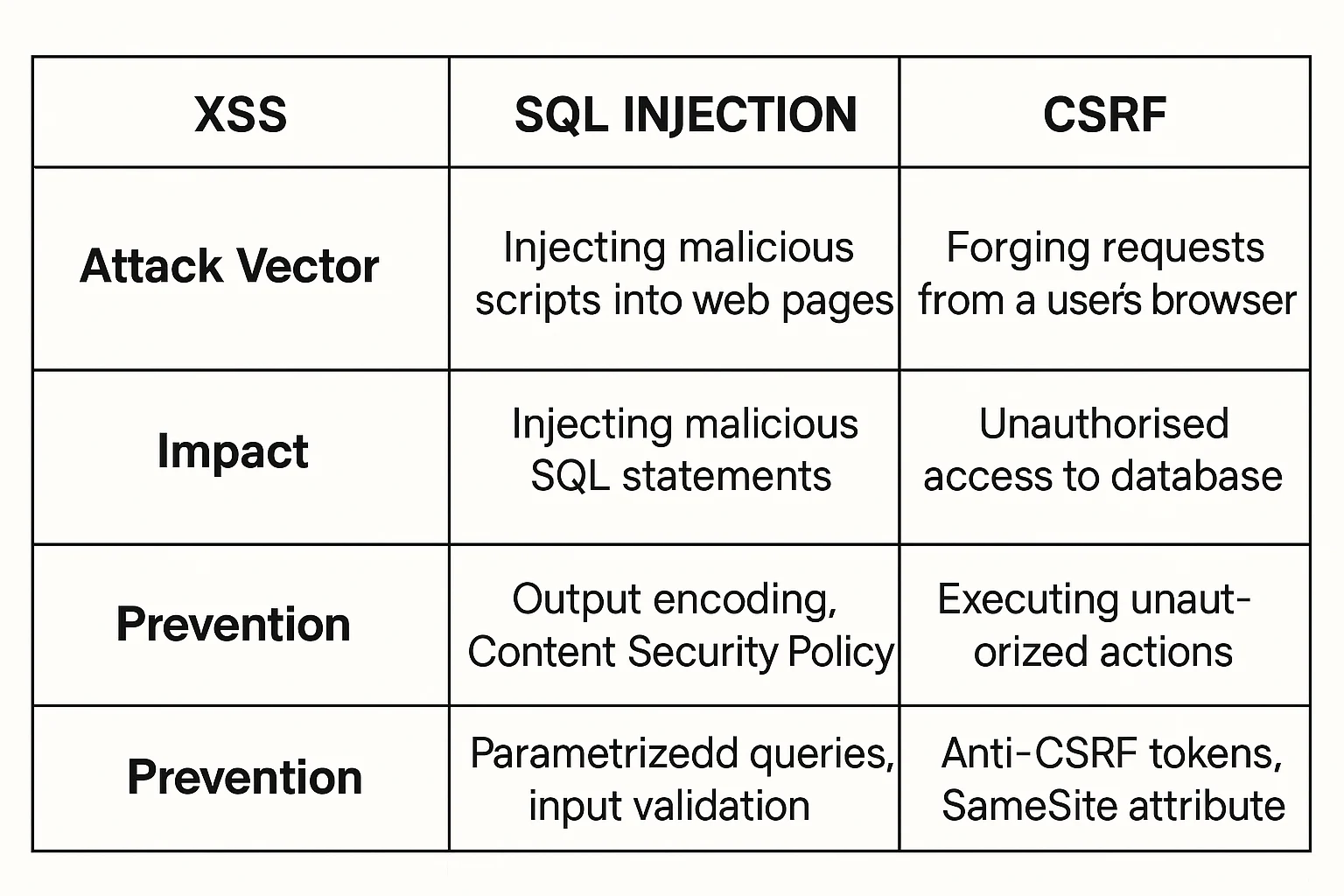
While XSS involves injecting malicious scripts that execute in users' browsers, other vulnerabilities like SQL injection target database queries, and CSRF tricks users into performing unwanted actions. Each vulnerability has distinct attack vectors, targets, and prevention strategies. Let's understand the difference between XSS and other types of attacks.
XSS vs. SQL Injection
These are both injection attacks, but they target different layers of the application:
- XSS targets the client side, injecting malicious code that executes in users' browsers
- SQL Injection targets the database layer, inserting malicious SQL queries that can extract, modify, or delete data
While XSS primarily impacts end-users by stealing their information or hijacking their sessions, SQL injection directly compromises the application's data integrity and confidentiality. The prevention strategies also differ significantly—XSS requires output encoding and content security policies, while SQL injection is prevented through parameterized queries and input validation.
XSS vs. Content/Script Injection
The difference between these two can be confusing because the terms are sometimes used interchangeably. However:
- XSS is specifically about injecting scripts that execute in another user's browser context
- Script injection can refer to any scenario where malicious code is injected into an application
In other words, XSS is a specific type of script injection that involves the "cross-site" element—where the script crosses from one user's context to another's.
XSS vs. CSRF
Cross-Site Request Forgery (CSRF) and XSS are often confused but operate in fundamentally different ways:
- XSS exploits the trust a user has in a website by executing malicious scripts
- CSRF exploits the trust a website has in a user's browser by forcing the browser to make unwanted requests
While XSS can be used to conduct CSRF attacks (by injecting scripts that make malicious requests), CSRF doesn't necessarily involve script injection. Instead, CSRF tricks authenticated users into performing unwanted actions on websites where they're logged in.
Meanwhile, CSRF is still a security concern. While modern security features like SameSite cookies have reduced the risk, CSRF vulnerabilities remain prevalent because they exploit the trust relationship more than XSS and require specific prevention mechanisms like anti-CSRF tokens.
Some of the preventive measures include JSON Web Tokens (JWTs), but they don’t prevent CSRF attacks alone. They need to be implemented alongside other protections. Similarly, SOP (Same-Origin Policy) provides some protection but isn't sufficient on its own to prevent all CSRF attacks.
Languages and Technologies Used in XSS Attacks
While JavaScript is the most common language used in XSS attacks due to its ubiquity in web browsers, other technologies include HTML, VBScript (in older IE browsers), CSS with specific exploits, and SVG elements with embedded scripts.
Here is how XSS attacks work with the technologies:
- JavaScript is the primary language used in XSS attacks due to its ability to manipulate the DOM, make network requests, and access sensitive browser data
- HTML can be used for certain types of attacks, especially when combined with event handlers
- VBScript was historically used in Internet Explorer (though this is largely obsolete now)
- CSS with certain browser-specific quirks can sometimes be used for limited attacks
- SVG elements with embedded scripts
The key aspect that makes JavaScript a security risk in this context is its dynamic nature and extensive browser API access. JavaScript can:
- Access cookies and local storage
- Make HTTP requests to any domain
- Modify the page content dynamically
- Access sensitive user information
- Interact with the browser's history and navigation
What is XSS Risk Assessment and it’s Impact
XSS vulnerabilities are typically classified as high-risk security issues due to their potential for data theft, account hijacking, malware distribution, and website defacement. The severity depends on the type of XSS, the sensitivity of the affected application, and what data/functionality an attacker can access. According to the OWASP Top 10—an authoritative ranking of web application security risks—injection attacks, including XSS, consistently rank among the most critical vulnerabilities.
What are the risks of XSS?
The potential impact of successful XSS attacks includes:
- Data theft: Attackers can steal sensitive information such as session tokens and cookies, authentication credentials, personal information, and financial data.
- Account hijacking: By stealing session information, attackers can impersonate legitimate users.
- Malware distribution: XSS can be used to deliver malware to visitors of the compromised site.
- Website defacement: Attackers can modify the appearance and content of websites.
- Network reconnaissance: XSS can be used to map internal networks and discover additional vulnerabilities.
The severity of an XSS vulnerability depends on several factors:
- The type of XSS (with stored XSS generally considered more severe than reflected)
- The sensitivity of the affected application.
- The data an attacker can access in the web application.
- How to exploit the application.
- Browser exploitation through chained attacks.
- Cryptojacking (unauthorized use of the victim's computer to mine cryptocurrency).
- Keylogging to capture passwords and sensitive information.
- Bypassing the multifactor authentication process in some scenarios.
- Social engineering attacks: use someone else's access to a compromised site.
What are the XSS Prevention Strategies and Best Practices
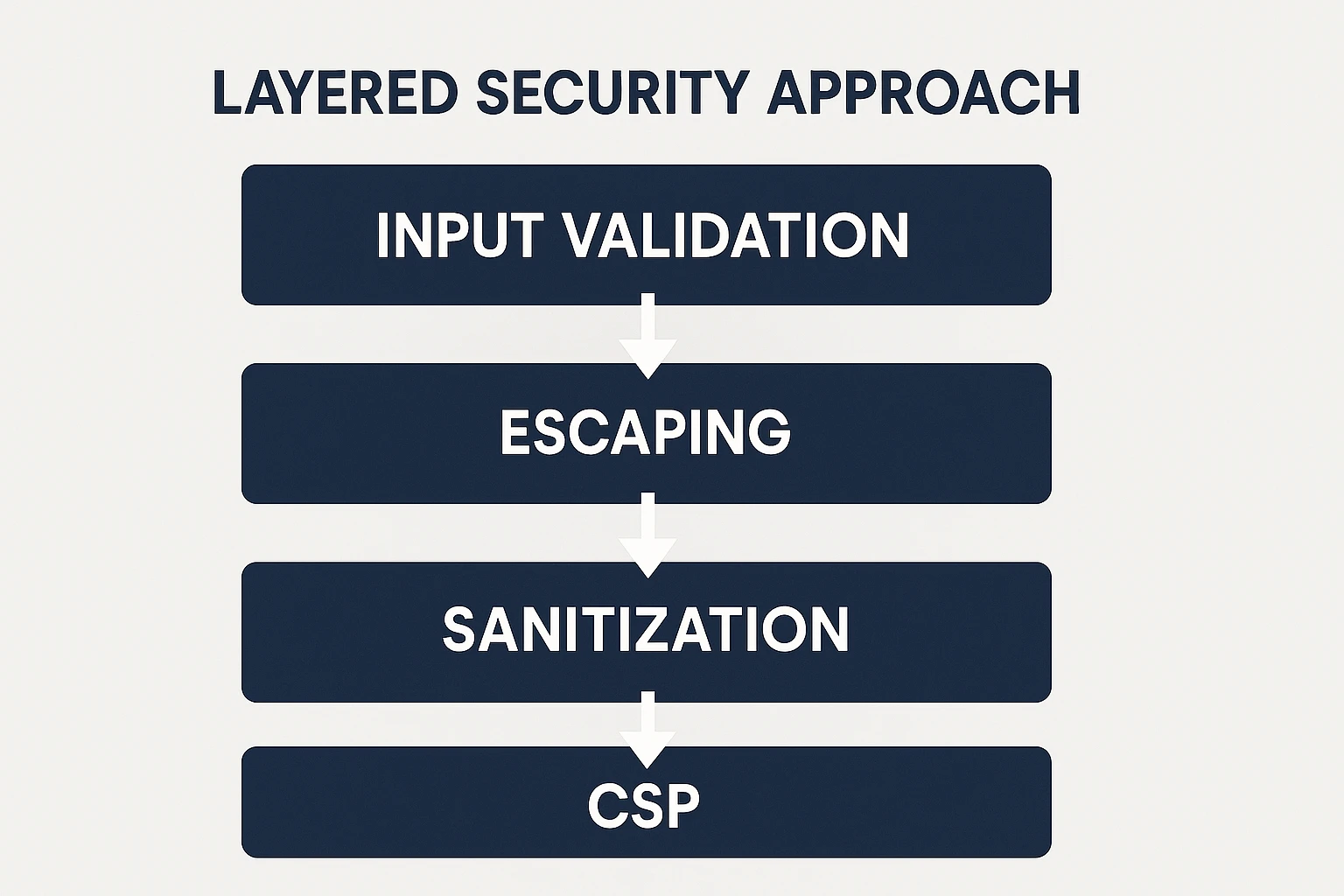
Use a defense-in-depth approach including input validation, output encoding specific to the context, Content Security Policy implementation, use of modern framework protections, secure cookie flags, and regular security testing.
Input Validation and Output Encoding
While there's no single universal function, proper output encoding is fundamental to XSS prevention. Different programming languages and frameworks offer specific functions:
- In PHP: htmlspecialchars() or htmlentities()
- In JavaScript: Libraries like DOMPurify
- In Java: OWASP ESAPI encoder functions
- In .NET: HttpUtility.HtmlEncode()
The above encoding isn't always sufficient.
What is an example of escaping XSS? Consider this PHP code:
// Dangerous (vulnerable to XSS)
echo "Welcome, " . $_GET['name'];
// Safer (with proper encoding)
echo "Welcome, " . htmlspecialchars($_GET['name'], ENT_QUOTES, 'UTF-8');
The second example properly encodes special characters that could be interpreted as HTML or JavaScript, preventing them from being executed as code.
Content Security Policy (CSP)
The Content-Security-Policy header is one of the most powerful tools for mitigating XSS attacks. It allows websites to declare approved sources of content that browsers should consider valid. A basic CSP that blocks inline scripts might look like:
Content-Security-Policy: default-src 'self'; script-src 'self' https://trusted-cdn.com
Modern Framework Protections
Modern JavaScript frameworks like React provide some inherent protection against XSS by automatically escaping values rendered in templates. However, they're not immune, especially when developers bypass their built-in protections. Methods like dangerouslySetInnerHTML can reintroduce XSS vulnerabilities if used carelessly.
Similar to React, Angular provides built-in sanitization to prevent XSS. It treats all values as untrusted by default and sanitizes them before insertion into the DOM. However, developers can bypass these protections using methods like bypassSecurityTrustHtml().
What are Other Additional Security Measures
- Secure cookie attributes: Using flags like HttpOnly and Secure can limit the damage of successful XSS attacks
- X-XSS-Protection header: While deprecated in modern browsers, it provides some protection in older ones
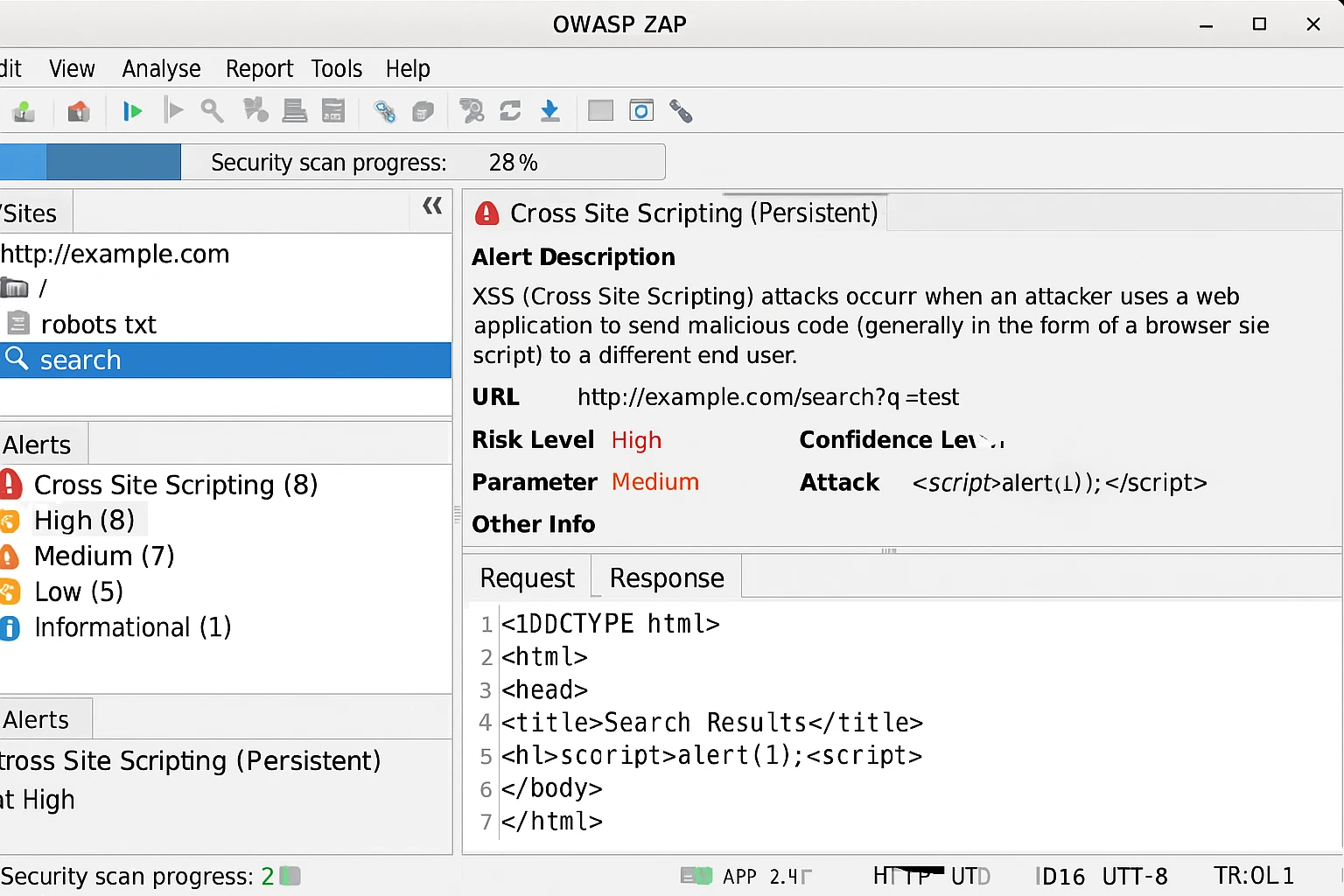
- Regular security testing: Using tools like OWASP ZAP or manual penetration testing
You need to understand that HTTPS encrypts data in transit but doesn't prevent XSS attacks. The malicious script still executes within the secure HTTPS context. Also, you should incorporate all the strategies mentioned above, along with developer education and security-focused code reviews.
XSS Detection and Testing
XSS detection involves both automated scanning using specialized security tools and manual testing techniques. Effective testing requires understanding common XSS patterns, bypass techniques, and knowing where to look for potential vulnerabilities in web applications.
How do you detect XSS?
Detecting XSS vulnerabilities typically involves using specialized security tools to identify potential injection points, carefully crafting payloads to test specific vulnerabilities, examining source code for improper handling of user input, and using dynamic analysis tools to monitor how data flows through the application.
Another tool is OWASP ZAP (Zed Attack Proxy), a popular open-source security tool used for finding vulnerabilities in web applications, including XSS. It provides the following features, such as automated scanning, manual testing support, traffic interception and modification, and contextual alerts based on risk level.
See Also: How to Test a Backend Application.
Beyond automated tools, effective XSS testing requires understanding common evasion techniques attackers use to bypass security filters, such as encoding variations, event handler injection, protocol-based attacks, and DOM-based manipulation.
When performing XSS testing, focus attention on search forms and fields, URL parameters, form inputs, file upload functions, user profile information, and comment sections. Threat modeling also helps to identify potential attack vectors, understand their impact, and prioritize security measures. While methodologies vary, a common approach includes identifying assets and entry points, creating an architectural overview, decomposing the application, identifying threats, and documenting vulnerabilities and mitigation strategies.
Conclusion
Cross-Site Scripting remains one of the most persistent security challenges in web development despite being well understood for many years. As we've explored in this article, XSS comes in multiple forms—reflected, stored, and DOM-based—each with its unique characteristics and attack vectors.
The pervasiveness of XSS stems from fundamental challenges in web development: the difficulty of properly validating user input, the complexity of modern web applications, and the powerful capabilities of client-side scripting languages like JavaScript. While frameworks and libraries have implemented various protections, XSS vulnerabilities continue to emerge as applications grow more complex.
Effective XSS prevention requires a defense-in-depth approach. No single technique—whether it's input validation, output encoding, or Content Security Policy—can provide complete protection on its own. Instead, developers must implement multiple layers of defense while maintaining awareness of emerging attack techniques.
For organizations serious about security, addressing XSS vulnerabilities should be part of a broader application security program that includes:
- Regular security testing.
- Developer education.
- Secure coding standards.
- Runtime protection mechanisms.
- Incident response procedures.
By understanding the nature of XSS attacks and implementing appropriate countermeasures, organizations can significantly reduce their risk exposure and protect both their systems and their users from this persistent threat.
Please Share.