Home > Edu-Tech > Phishing in Cybersecurity: How to be Protected from Digital Deception
Phishing in Cybersecurity: How to be Protected from Digital Deception
Phishing is a cybercrime technique where attackers impersonate legitimate organizations to steal sensitive information such as usernames.
By :Thomas Inyang🕒 25 May 2025

Introduction
You got an email from your bank asking you to "verify your account immediately" to avoid suspension. The message looks legitimate, uses your bank's logo, and creates a sense of urgency. You click the link, enter your credentials, and unknowingly hand over your financial information to cybercriminals. You've just experienced a phishing attack, which is the most common and successful cyberattack method that affects millions worldwide.
In 2024, phishing attacks increased by 61% compared to the previous year, with cybercriminals stealing over $12.5 billion globally. But what makes this guide unique is that it not only defines phishing, but also gives you practical information, real-world examples, and tried-and-true strategies that security professionals use to stay safe.
If you're an IT professional protecting your network, a business owner protecting your company, or just someone who wants to browse the internet safely, this thorough guide will turn you from a potential victim into an informed digital defender.
At the end of this guide, you will discover:
- How to identify complex attacks that deceive even tech-savvy users,
- Understand the psychological tricks used by criminals.
- How multi-layered security measures can be put into practice.
Understanding Phishing
Phishing is a cybercrime technique where attackers impersonate legitimate organizations to steal sensitive information such as usernames, passwords, credit card details, or personal data through deceptive communications.
Although many people believe that phishing is just "fake emails," the truth is much more complex. By playing on our emotions, fabricating a sense of urgency, and taking advantage of our trust, modern phishing attacks circumvent our innate skepticism.
Cybercriminals use seductive lures to "catch" victims, much like fishermen use bait to catch fish. That's where the term "phishing" comes from. But unlike fishing, where the fish has no choice once hooked, you can always recognize and avoid these digital traps.
Phishing is extremely dangerous because it is not malware or a virus in the traditional sense. It's a cyberattack that typically relies on tricking you into providing information voluntarily, though it can also lead to the installation of malware. Even the most advanced security systems cannot prevent a user from willingly entering their password on a fraudulent website, which makes it incredibly effective due to the human element.
Phishing attacks usually have three main goals: obtaining access to valuable systems and data (corporate espionage or ransomware deployment), obtaining immediate financial gain (direct money theft), or long-term financial exploitation (identity theft).
Understanding this foundation helps us transition to examining the real-world impact and sophisticated methods criminals employ today.
Real-World Impact of Phishing
Phishing consequences range from individual financial loss and identity theft to massive corporate data breaches affecting millions of customers and costing companies billions in damages.
Take Anthem Inc., one of the biggest health insurers in the United States, as an example. In 2015, hackers gained access to 78.8 million customers' personal information through a single spear-phishing email sent to an employee. Anthem spent over $115 million on legal settlements and remediation efforts as a result of the attack. This was not some complicated technical trick, but a convincing email that seemed to come from a trustworthy source.
The 2020 Twitter Bitcoin scam served as a recent example of how social engineering can jeopardize even the most security-conscious companies. Attackers persuaded Twitter staff members to grant access to internal systems via phone-based phishing, or vishing. Resulting in the compromise of well-known accounts belonging to Bill Gates, Elon Musk, and Barack Obama.
See Also: XSS Attack and How to Prevent it
However, big businesses are not the only ones affected by phishing. 43% of cyberattacks target small businesses, making them more vulnerable. Small businesses frequently lack the resources to implement comprehensive protection, which makes them appealing targets for criminals. This is in contrast to large enterprises that have dedicated security teams.
The psychological effects on specific victims are just as important. Victims frequently endure anxiety, embarrassment, and long-term trust issues with digital communications in addition to monetary losses, which average $1,200 per incident. People are now extremely cautious when using the internet, which limits their ability to take advantage of trustworthy digital services.
This practical effect emphasizes how important it is for everyone's online safety to comprehend the different kinds of phishing attacks.
Types of Phishing: Know Your Enemy
Phishing attacks are categorized by their targeting method, communication channel, and level of personalization, ranging from mass email campaigns to highly targeted attacks against specific individuals or organizations.
Email Phishing
Traditional email phishing remains the most common attack vector, representing 83% of all phishing attempts by casting a wide net, sending thousands of generic messages hoping to catch a few victims. Common examples include fake notifications from banks, social media platforms, or popular services like Amazon or PayPal.
Spear Phishing: Precision Targeting
Unlike broad email campaigns, spear phishing targets specific individuals or organizations. Attackers research their victims through social media, company websites, and public records to create highly personalized messages. These attacks have a 70% higher success rate than generic phishing because the personalization makes them appear legitimate.
Whaling
Whaling specifically targets high-value individuals like CEOs, CFOs, or other executives. These attacks often impersonate board members, legal counsel, or regulatory authorities to create urgency and bypass normal verification procedures. The average whaling attack costs organizations $1.8 million.
Smishing and Vishing
Smishing (SMS phishing) exploits our trust in text messages, while vishing (voice phishing) uses phone calls. These methods are increasingly effective because people tend to trust phone communications more than emails. A common smishing example is fake package delivery notifications, while vishing often involves fake tech support calls.
QR Code Phishing
QR code phishing (quishing) has emerged as attackers exploit our growing comfort with QR codes post-pandemic. Malicious QR codes can redirect users to fake websites, automatically download malware, or initiate unwanted actions. Since most people can't "read" QR codes visually, they represent a significant blind spot in security awareness.
Knowing these attack types naturally leads us to investigate how criminals use technology to enhance the credibility of their deceptions.
The Technology Behind Deception
To produce realistic impersonations of trustworthy companies and people, modern phishing uses advanced technical techniques such as domain spoofing, email header manipulation, and social engineering frameworks.
You might be surprised at how sophisticated modern phishing attacks are technically. Criminals no longer use crude forgeries or glaring misspellings. Instead, they use cutting-edge methods that can deceive even users who are concerned about security.
Domain Spoofing and Typosquatting involve registering domains that closely resemble legitimate ones. For example, "arnazon.com" instead of "amazon.com" or "paypaI.com" (using a capital 'i' instead of a lowercase 'l'). These minor differences are often missed, especially on mobile devices where fonts may be small.
Email header manipulation allows attackers to make emails appear to come from trusted sources. While the actual sending server might be located anywhere in the world, the displayed "From" field can show any name or email address. This is why checking email headers and sender verification is crucial for security professionals.
Clone phishing represents a particularly insidious approach where attackers intercept legitimate emails, modify them slightly to include malicious links or attachments, and resend them from similar-looking addresses. Recipients often assume they're receiving the same message twice, making them more likely to click without scrutiny.
It's critical to realize that phishing is a general attack strategy that may use spoofing among other tactics, whereas spoofing is a technical technique that involves impersonating the communication source. Similarly, spam and phishing emails are different. Spam is unsolicited bulk emails, usually advertising, whereas phishing focuses on using deception to steal money or information.
We can better understand why particular individuals and organizations become targets thanks to these technological capabilities that allow criminals to target victims with previously unheard-of precision.
Why You Might Be Targeted
Phishing targeting is based on factors including perceived value (financial assets, data access, or influence), vulnerability indicators (public information, security posture, or behavioral patterns), and accessibility through various communication channels.
Understanding why attackers choose their targets can help you assess your risk level and take appropriate precautions. Contrary to popular belief, you don't need to be wealthy or hold a high-profile position to become a target.
Individual targeting factors include having active social media profiles that reveal personal information, recent life changes (new job, moving, marriage) that create verification opportunities for criminals, or simply being part of a demographic that frequently engages with digital services. Seniors are often targeted because they may be less familiar with digital security practices, while millennials are targeted because they conduct most of their business online.
Professional risk factors significantly increase targeting likelihood. If you work in finance, healthcare, education, or government, you're more likely to be targeted because of the valuable data you can access. Employees with system administrator privileges, HR personnel with access to employee data, or anyone involved in financial transactions represent high-value targets.
Behavioral Vulnerability Indicators that criminals look for include sharing too much information on social media, using the same password across multiple accounts, clicking on links without verification, or having a history of engaging with suspicious emails. Attackers often purchase lists of previous phishing victims because these individuals have demonstrated a willingness to engage in deceptive communications.
See Also: Cross-Origin Resource Sharing (CORS): What You Need To Know.
The psychology behind successful phishing attacks reveals why even security-aware individuals sometimes fall victim. Criminals exploit cognitive biases like authority (impersonating bosses or officials), urgency (creating false deadlines), and social proof (suggesting others have already taken the requested action).
This targeting method makes recognition skills essential for everyone's digital safety.
How To Identify Phishing Attacks
Phishing recognition is the process of systematically assessing the sender's legitimacy, the content of the message, and the actions that are requested to spot suspicious communication patterns, technical irregularities, and psychological manipulation techniques. Even with the ongoing advancements in security technology, successful attacks are still largely prevented by human awareness.
Email red flags include urgent language demanding immediate action, generic greetings like "Dear Customer" instead of your actual name, requests for sensitive information via email, mismatched URLs (hover over links to see the actual destination), and poor grammar or spelling in communications supposedly from professional organizations.
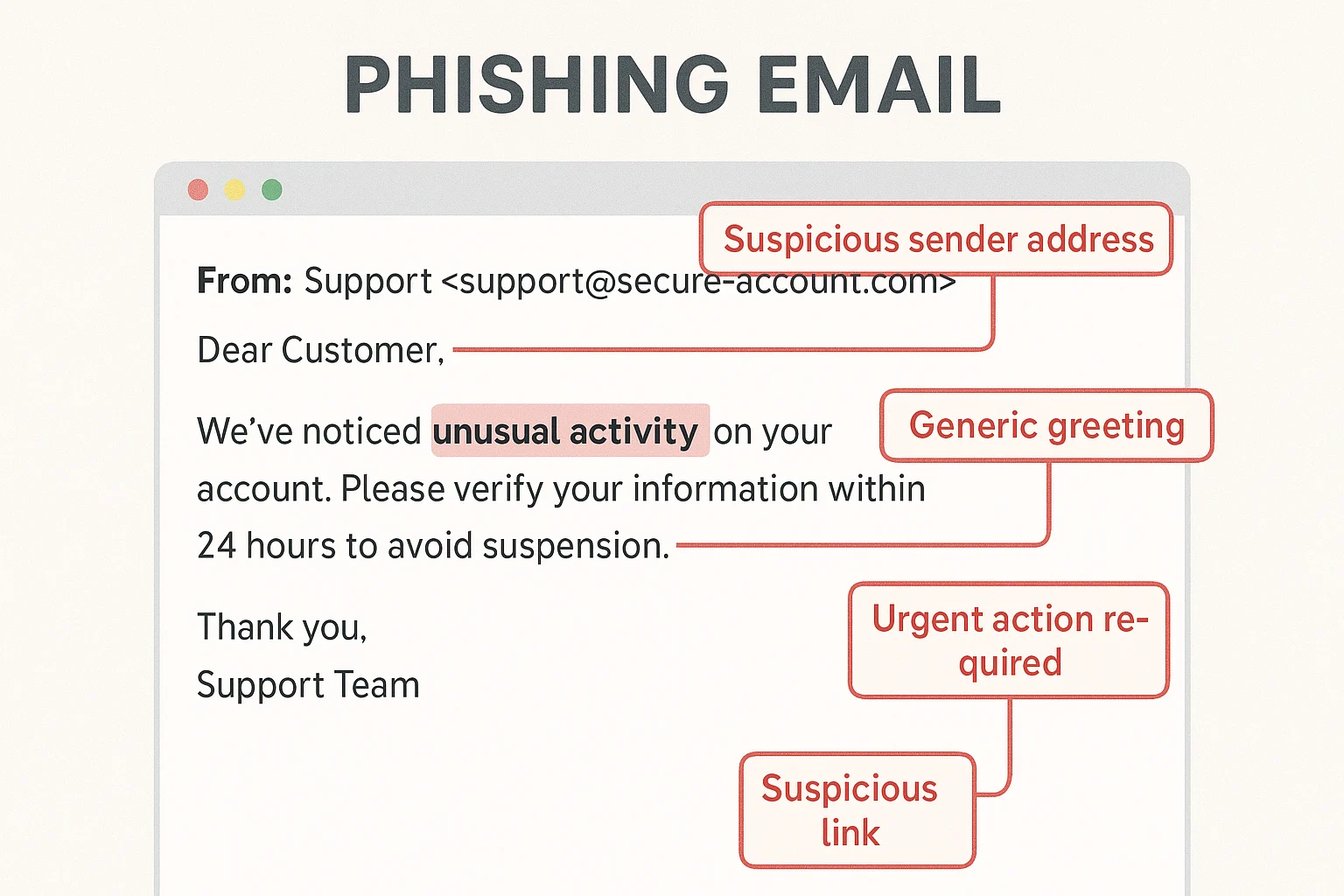
The Three Most Important Warnings Immediate threats of account closure or legal action, links or attachments from unidentified or dubious sources, and unexpected requests for financial or personal information are all warning signs that should startle suspicion. Before acting, pause and confirm through separate channels if a communication contains any of these components.
For those seeking more protection, Advanced Detection Techniques include using online tools to safely analyze suspicious links, checking email headers for routing information, and confirming digital signatures when available. Often, the most telling sign of a phishing email is a mismatch between the request and the context. For instance, your bank might ask for information that they already have, or a service you have never used might say that your account needs to be verified.
Malicious links are a major attack vector, so URL analysis requires extra care. Hover your cursor over any link before clicking it to view the destination. Check for minor typos in the domain name, odd top-level domains (such as “.tk or .ml” in place of .com), or overly complicated URLs that consist of numerous redirects. For customer communications, legitimate businesses usually use clear, easily identifiable URLs.
Instead of using the contact information in the suspicious message, the best course of action when you receive a malicious, unexpected request for information or action is to get in touch with the organization directly using a phone number or website address you trust.
Understanding the legal and criminal aspects of phishing attacks makes these recognition skills even more valuable.
Law Enforcement Reaction to Phishing and Legal Repercussions.
In the majority of countries, phishing is considered a federal offense, with severe fines and jail time as possible punishments. Law enforcement agencies use advanced methods to find and apprehend cybercriminals worldwide.
In the United States, phishing falls under multiple federal laws, including the Computer Fraud and Abuse Act, which can result in up to 20 years in prison for repeat offenders. The average sentence for convicted phishing criminals is 4-6 years, with financial restitution often reaching millions of dollars.
International cooperation has improved significantly, with agencies like the FBI's Internet Crime Complaint Center (IC3), Europol's European Cybercrime Centre, and Interpol working together to track criminals across borders. Despite the global nature of phishing, successful prosecutions have increased by 40% over the past three years as law enforcement develops better tracking capabilities.
Tracking and investigation of phishing attacks is more advanced than many criminals realize. While they may use VPNs, temporary email addresses, and cryptocurrency, digital forensics experts can often trace attacks through blockchain analysis, traffic correlation, and social engineering intelligence gathering. However, prosecution rates remain low (approximately 5% of reported cases) primarily due to the international nature of many attacks and resource limitations.
See Also: Input Validation and Its Importance in Software Development
Reporting mechanisms are crucial for building cases against cybercriminals. In the US, report phishing to the Federal Trade Commission, FBI's IC3, and the Anti-Phishing Working Group. Many email providers also have built-in reporting features that help identify and block similar attacks. While individual reports may not lead to immediate arrests, they contribute to larger investigations and help protect others.
It is easier to understand why prevention and response tactics are so crucial for both individuals and organizations when one is aware of the criminal nature of phishing.
How to Prevent Phishing Attacks
Effective phishing prevention requires layered security combining technological solutions (email filters, authentication systems, and security software) with human awareness training and organizational policies to create comprehensive protection against evolving attack methods. Prevention is always more effective and less costly than recovery.
Technical solutions form your first line of defense. Modern email security gateways can block 99.5% of known phishing emails before they reach your inbox. Enable two-factor authentication on all of your important accounts so that thieves cannot access them without the second authentication factor, even if they manage to steal your password. Use browsers with integrated phishing protection, such as Firefox's Enhanced Tracking Protection or Chrome's Safe Browsing, and make sure your browsers are up to date with the most recent security patches.
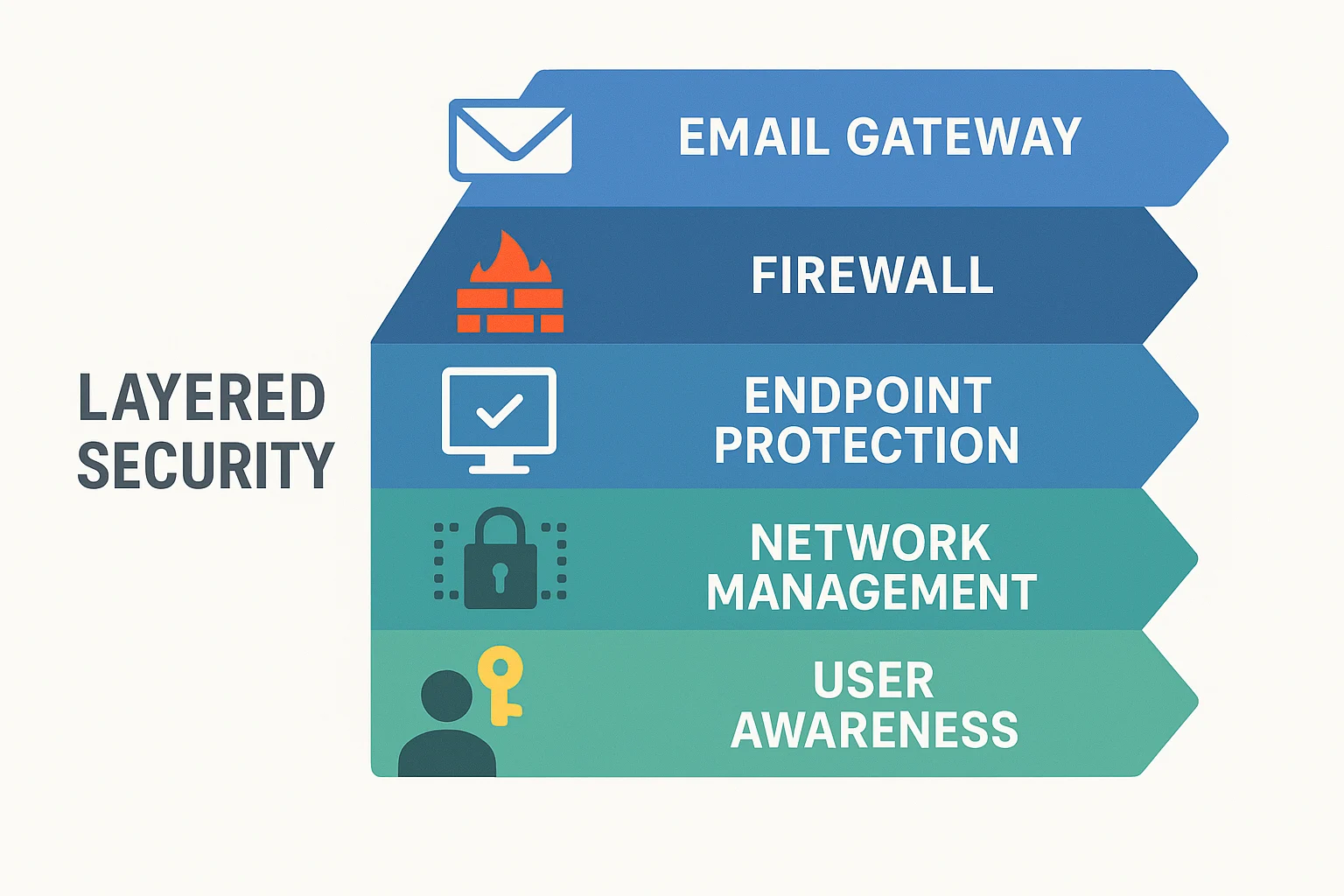
The two most successful prevention strategies are human awareness training and technological filtering. While most attacks can be prevented by technology, sophisticated attempts that evade automated systems require human judgment to be detected. In companies that have comprehensive programs in place, regular security awareness training can reduce successful phishing attacks by as much as 80%.
Personal Security Habits that significantly reduce your risk include never clicking links in unexpected emails (instead, navigate to websites directly), verifying unexpected requests through independent communication channels, keeping software updated with automatic updates enabled, and using unique, complex passwords for different accounts with a password manager to maintain them securely.
Organizational Policies should include clear incident reporting procedures, regular phishing simulation exercises, and defined response protocols when employees suspect they've encountered phishing attempts. Companies with strong security cultures experience 70% fewer successful attacks than those without formal security awareness programs.
Even with strong prevention measures, incidents can still occur, making response and recovery planning essential components of comprehensive security.
Response and Recovery When Prevention Fails
Phishing incident response involves immediate containment actions to limit damage, systematic recovery procedures to restore security, and long-term monitoring to prevent future exploitation of compromised information or systems.
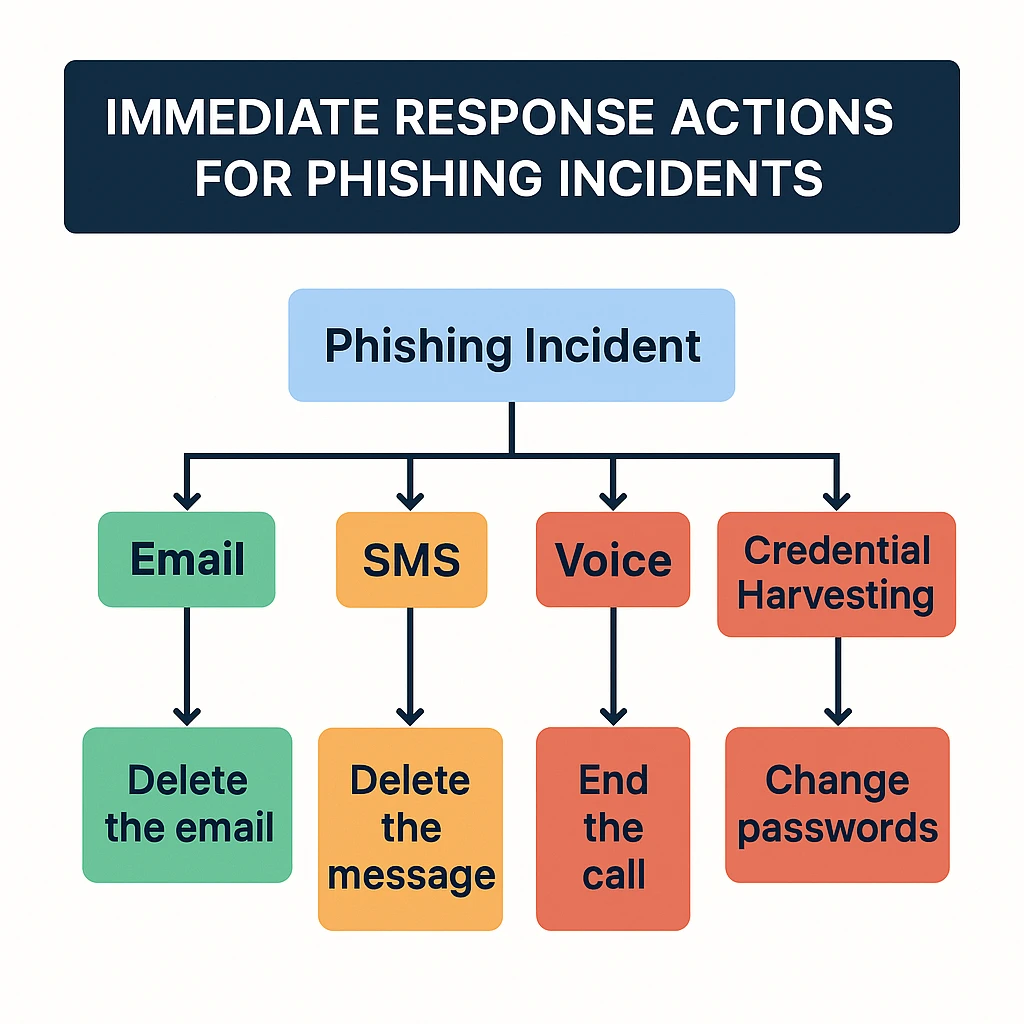
Despite the best prevention efforts, successful phishing attacks do occur. Your response in the first few hours can significantly impact the ultimate damage and recovery time.
Immediate Response Steps, if you suspect you've been phished, include changing passwords immediately for any accounts where you entered credentials, checking recent account activity for unauthorized transactions or changes, running a complete antivirus scan if you downloaded anything, and notifying your bank or credit card companies if financial information was compromised.
How to Know You've Been Compromised includes obvious signs like unauthorized charges or account changes, as well as subtle indicators such as friends receiving strange messages from your accounts, slower computer performance, unexpected pop-ups or toolbars, or being locked out of accounts you didn't change. Many victims don't realize they've been compromised until weeks or months later when damage becomes apparent.
Email Management: After a phishing incident, deleting suspicious emails from your inbox doesn't prevent them from being sent to others, but it does remove them from your device. Most modern email providers, like Gmail, automatically move confirmed phishing emails to spam folders and use the information to improve filtering for all users.
Long-term recovery may entail continuing watchfulness for indications of abuse, identity theft protection services, and credit monitoring. Keep track of everything associated with the incident, such as email headers, screenshots, and any financial effects for future law enforcement or insurance claims.
Professional vs. Personal Incidents require different response approaches. If the phishing occurred on a work device or involved work accounts, immediately notify your IT security team. Many organizations have specific protocols and legal requirements for reporting security incidents, and early notification can prevent broader network compromise.
Staying Ahead of Phishing Threats and Continuous Protection
AI-powered phishing is the future. Criminals now use artificial intelligence to create more convincing messages, personalize attacks at scale, and even generate realistic voice clones for vishing attacks. These AI-enhanced attacks can analyze your writing style from social media posts and create messages that match your communication patterns, making them incredibly difficult to detect.
As hackers embrace new technologies and take advantage of new channels of communication, the phishing landscape is changing quickly. Understanding these trends and modifying your defenses appropriately is essential to staying safe.
Emerging attack vectors include taking advantage of virtual reality environments, gaming platforms, cryptocurrency exchanges, and smart home appliances. Every connected platform and gadget we use increases the risk of social engineering attacks. QR code phishing will probably spread beyond straightforward website redirects to incorporate location-based attacks and augmented reality overlays.
Strategies for continuous protection must change to reflect the changing nature of threats. This includes reviewing and updating your security procedures regularly, staying up to date on current threats through reputable security news sources, and scheduling regular security awareness training that covers new attack types. If you want to stay up to date on the most recent attack trends, think about signing up for threat intelligence services or following trustworthy cybersecurity groups.
Building security resilience entails developing routines and procedures that can change to meet emerging threats. This entails developing a personal security culture that puts protection first without becoming paranoid, diversifying your information sources for verification, and keeping a healthy skepticism about unexpected communications, no matter how authentic they seem.
Understanding that phishing prevention is a continuous process of awareness, adaptation, and improvement rather than a one-time event is crucial for long-term security.
Conclusion
Phishing attacks will continue evolving, but your understanding and defensive capabilities can evolve faster. The knowledge you've gained from this guide provides a solid foundation for recognizing and preventing the vast majority of phishing attempts you'll encounter.
Remember the key principles: verify before you trust, think before you click, and when in doubt, seek independent confirmation. Technology can provide significant protection, but your awareness and judgment remain the most important factors in staying safe online.
Your investment in learning about phishing will pay off in terms of your peace of mind and personal security. Tell your friends, family, and coworkers about this; cybersecurity works best when whole communities comprehend and follow sound security practices.
Remain alert, educated, and, above all, safe in our increasingly interconnected world. You are now in control of your digital security and have the means to properly safeguard it.
For the latest updates on phishing threats and protection strategies, bookmark this guide and check back regularly as we update it with new information and emerging trends.